I came across an article earlier today that said the Planned Parenthood hack looked an awful lot like a PR stunt, and pointed to some screenshots and code as evidence. I was curious, so I dug around to see if I could find anything that indicated it was a PR stunt. See, I have no love for Planned Parenthood or the atrocities they commit on unborn children, but I don’t want false accusations or unproven conspiracies clouding my very legitimate arguments with the organization. So, was the hack a PR move?
Short answer: Probably not.
Longer, more technical answer:
I did a bit of digging. As of the publishing of this article, Plannedparenthood.org currently points to 54.230.194.219, which is an Amazon Cloudfront address; however, as of a few days ago, their IP address was 66.151.111.231, the IP address for a smaller ISP called Hedgehog Hosting. (You can see the full DNS record history here.)
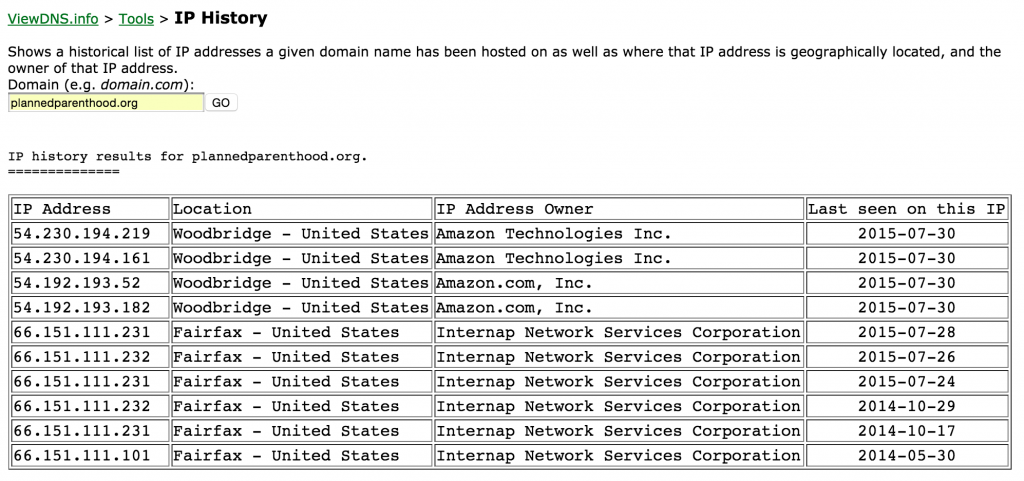
It’s pretty standard practice for large organizations to have an “Under Maintenance” page that gets put up in case of server problems. If something happens with your server, you can either redirect all traffic to that page on the server, or put it up elsewhere and point all traffic to it. The fact that they recently changed the DNS to point to Cloudflare (which is much more resilient to attacks) seems to indicate that they switched the DNS over for this maintenance page.
The Federalist article brings up the fact that some secure.ppaction.org pages still work, even though ppaction.org shows the aforementioned maintenance page. Checking the DNS records actually reveals that secure is actually a subdomain that seems to be mapped to a different IP address (a “constituent relationship management solution” called Convio), which would explain why that was still up when the main domain wasn’t. Indeed, curling the main site reveals that there’s a 301 redirect back to plannedparenthood.org, which makes sense—they wouldn’t want people hitting that domain directly.
I should point out that this could still in theory be a marketing stunt: they could have moved over to Amazon and crippled their old server to draw attention to the hack that took place on Sunday. However, the DNS records are consistent with real server problems (and something I’ve done when I’ve had problems before).

